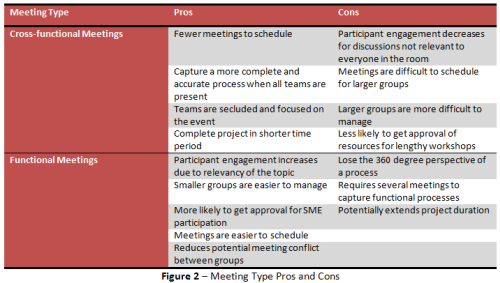
Organizations are increasingly looking to improve their processes and additionally embrace digital transformation to leverage their capabilities. Two frameworks that have gained traction in this regard are the Business Process Maturity Model (BPMM) by the Object Management Group (OMG) and the Digital Transformation Framework (DTF) used by Laserfiche. While both frameworks aim to enhance efficiency and effectiveness, they differ in their approach. In this blog post, we will explore what these frameworks are and how they align (or not) so that you will be able to be wiser when choosing transformation frameworks.
The Business Process Maturity Model (BPMM) is a framework that assists organizations in assessing their business processes against five levels of maturity. It assists in identifying areas for improvement and developing a roadmap for process improvement. It also provides a common language for process redesign and some government organizations require a certain level to consider an organization’s tender submission.
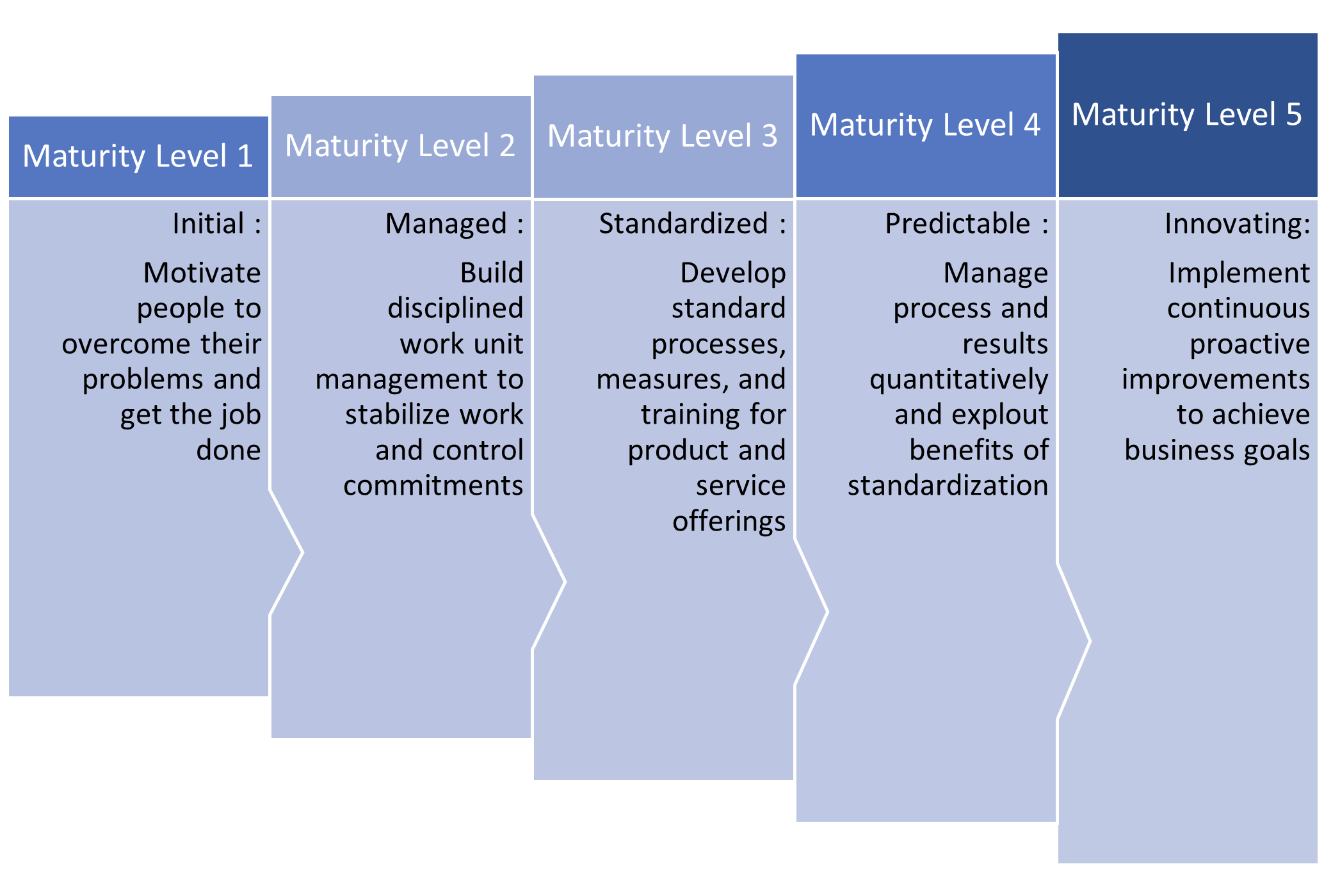
The BPMM consists of five levels of process maturity, which are as follows:
Initial: This level represents an ad hoc approach to process management, where processes are informal. The success of the work depends on the employee who just gets the job done and this results in inconsistent outcomes.
Managed: At this level, basic processes are documented, and some level of standardization and consistency is achieved but this is sporadic and will depend on the management of that unit. The benefits of process improvement begin to seep in, for example reducing rework.
Standardized: This level represents a structured approach to process management, where end-to-end processes are well-defined and documented, thus removing the silo effect. This includes process measures and using best practices to define processes.
Predictable: At this level, process performance is measured and monitored. The processes are automated and stable with predictable results. Knowledge is gained when quantitatively managing processes, for example, optimally achieving capacity.
Innovating: This level represents a proactive organization with a strong culture of process change while implementing and planning continuous improvement. This results in finding new and better ways to provide value to the client.
Advertisement
The other focus organizations have, is to achieve their digital transformation goals and drive innovation in the digital age. This has a larger scope than just processes. “Laserfiche is the leading global provider of intelligent content management and business process automation. The Laserfiche® platform enables organizations in more than 80 countries to transform into digital businesses”. Their Digital Transformation Model (DTM) provides a structured framework for content digitization and process automation through to data-driven innovation.
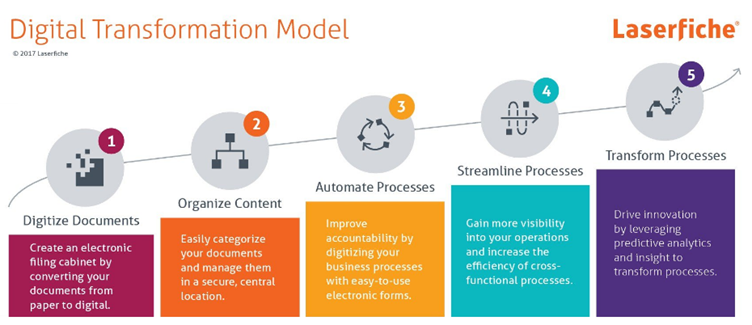
The Digital Transformation Model consists of five levels, which are as follows:
Digitize Documents: Converting paper documents to electronic documents. This leads to cost savings and less chance of lost data, but there is no central repository and so the information is fragmented, especially between silos.
Organize Content: Categorizing and organizing documents into a central repository to increase accessibility and improve security. For example, invoices are filed under the accounts payable folder. This organizing of documents assists in streamlining the work being done and supports compliance. It should be noted that at this point the document storage is standardized but the work being done is not yet standardized.
Automate Processes: Eliminating inefficient processes such as paper forms and replacing them with standardized electronic forms. Automation leads to improved productivity, accountability, and capacity but still lacks visibility because the automation is sporadic, and the end-to-end processes have limited visibility.
Streamline Processes: Automating common processes (not just forms) to increase visibility and gain business insights, for example, to optimize staffing levels. At the end of this phase, the company will be able to implement streamlined processes easily, have access to complete and consistent data, measure progress using tools like dashboards and visualizations, and involve customers in the process.
Transform Processes: Align processes with business needs, make plans for the future, and become more proactive. Data-driven innovation can be done by leveraging analytics and the organization will be more agile in changing markets.
The frameworks align by focusing on enhancing process efficiency and effectiveness. There is a strong emphasis on the role of technology (such as a central repository) as well as process management concepts (such as end-to-end processes and standardized processes). They both have five levels to compare.
However, there is a major concern with implementing these transformation frameworks and that is when to automate processes and when to standardize them. In the process maturity model framework above, the standardization starts at level 2 and is completed at level 3, while process automation takes place at level 4. In Laserfiche’s digital transformation framework, automation takes place at level 3 and processes are only improved and standardized at level 4. This means by following both transformation initiatives at the same time, the organization is working at cross-purposes, and it is likely that both projects will fail, resulting in a very costly mistake for the organization.
It should also be noted that with the digital transformation framework, there is no initial level where the company is purely paper based. It would make sense that before the digitalization level, there would be a level where the organization is haphazard about its use of technology. This may result in a six-level model and so not aligned with the levels of the process maturity model again.
In conclusion, there are many other business process maturity model frameworks (Robledo, Gartner, CMMI, and Rosemann) and other digital transformation frameworks (for example McKinsey, Forrester’s Playbook, and Capgemini). Whichever you choose, make sure your transformation frameworks align before sinking billions into organizational transformation projects that are heading in opposite directions.




 Figure 1 – Levels of Process Maps
Figure 1 – Levels of Process Maps